The latest iOS jailbreak was released yesterday. Called “evasi0n” it can be used to bypass most all protections in iOS 6.1 on any device that supports it. It’s quite cool, and was certainly something I was looking forward to (since much of my work is greatly aided by working on a jailbroken device).
However, another part of my work is ensuring that our customers’ devices are as secure as they can be. And having an available jailbreak kind of weakens those assurances. So it might be useful to find a way to prevent the jailbreak from working.
And, it turns out, there might be such a way. At least, until the jailbreak team finds a workaround for the workaround.
Last March, Apple released the Configurator Application. Using this application, iOS devices can be put into a “Supervised” mode, strongly locks down many features. One of these features is the ability to connect to iTunes and do backups/restores. On a supervised device, this functionality is possible only from the machine designated as the device’s supervisor.
The evasi0n jailbreak just happens to depend on the iOS backup / restore channel. So much so, in fact, that this is what I got when I tried to jailbreak a supervised device:
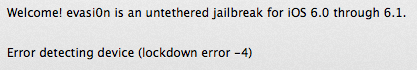
Could the evasi0n authors work around this? Possibly. It depends on how deep the supervised mode controls are embedded within iOS. If the device requires a unique host key (from the supervising machine) in order to restore data to the iPad, then it could well be impossible to make evasi0n work on anything other than the actual supervising host.
Of course, putting a device in supervised mode isn’t for the faint of heart – it’s a major shift in how one configures and manages iOS devices. So this probably won’t be a “Jailbreak Stopper” for every major organization out there with large pools of iPads. But it might provide some additional comfort in small groups, like iPads checked out to executives, etc.
But couldn’t a user just remove the device from supervision? Yes, but that’s harder than it sounds. “Erase all Settings” won’t do it, and even “Erase all content and settings” (essentially, “wipe the device with extreme prejudice”) won’t kill the supervisory link. To make a device unsupervised, you need to connect it back to the supervising machine, and sever the link within Configurator. You should also be able to do it in iTunes by doing a full OS restore. In either case, however, all data on the device is wiped, so anything installed while in supervised mode would be lost prior to the jailbreak.
Bottom line: if your organization has iOS devices with sensitive information, and you’re concerned that this jailbreak might put data at risk, it might be worth checking out Configurator and putting some of your devices under supervised control.
[shameless plug: I’ll be talking a little about this, and other ways to protect your data on iOS, at ShmooCon.]
UPDATE: Further thought should’ve made it obvious to me that forcing encrypted backups would have the same effect, and this is borne out in some simple testing. Of course, the user can’t be permitted to remove the encryption: so it needs to be forced through a configuration profile, preferably one that can’t be removed. If this setting is implemented through Mobile Device Mangaement, then the user could remove the device from MDM, disable encryption, jailbreak the device, and then re-enroll in MDM. So not entirely foolproof, but perhaps a more practical approach than shifting everyone to supervised mode.


