DBIR Cover Challenge 2013
It’s time for the 2013 edition of the Verizon Data Breach Investigation Report Cover Challenge! This year I didn’t win…but only just barely. It also felt like a bit of a different puzzle this year, not quite as much a series of challenges as just a scavenger hunt with only the barest minimum of breadcrumbs scattered to help us follow the path to victory.
With that in mind, I’ll focus less on the individual puzzle elements, and more on the challenge experience.
My big takeaway this year is: Discipline. Time and again, I found myself stuck, and rather than taking the right approach and stepping back for a moment, I just spun my wheels and got nowhere. While this is well-known weakness of my puzzle-solving skills, it felt more troublesome than usual this time around. Perhaps because each stage had so few obvious next-steps, that once I found the first (obvious) angle, I stopped looking for others. Or perhaps everything was perfectly obvious, and I just Wasn’t Paying Attention. Either way, I know I missed many things along the way, and was lucky to even pull out 2nd place.
The puzzle started, for me, about 9:00 on a Monday night (this particular Monday was April 22). The first thing I did was to try to find hidden text in the report, first by doing a “select all” and copy/paste, then using command line utilities pdf2text and pdf2html. The only thing I found was a single hash: "f38b8e92f812 f9f4f26be4793827d906." For some reason, I kept getting it copied out with a break in the middle, so I wasn’t sure if it was a single 16-byte string, or a 6-byte and 10-byte together (like a salt and hash).Either way, I couldn’t find any online databases that knew what it was.
I also looked through the document for interesting links, or silly sidebars (like last year’s “Chuck Testa” commentary). I found a github site with a couple of tools put out by the Verizon Risk team, but not much else. Then late that night, the @VZDBIR Twitter feed announced that there was a problem with the document, that something was missing, and they’d post a new version in the morning. What was missing? Usually there’s a big block of hidden encoded text, and I didn’t see anything like that this time. Or perhaps the (fragmented?) hash was an incomplete part of a longer list of hashes, or any of a million things.

Tuesday morning, they published the new version, and immediately I discovered a JPEG image hidden in a large block of base-64 encoded, hidden text. The image sent me to the same github account I’d found the night before, so I spent a little time looking for easy signs of steganography in this image, to no avail. I glanced again at the two repositories, then looked at the account avatar, and noticed that the background was transparent, but there was a solid white block at the bottom. I verified that this appeared to contain some kind of hidden data, and spent some time trying to extract that, or to re-format the size of the image to get something visually recognizable out of it. In the end, I never did figure out what was supposed to be in there. (Incidentally – I just heard from someone on the VZ-Risk team, and he had no idea what was in there, saying “That image had been there long before we planned out this challenge.” So…anyone want to try to figure that one out? The original, and data extracted from the white footer bar, are included below.)
![]()

So the grand total progress I had made, after 24+ hours, was: I’m on a github site. Which I’d first visited within probably 20 minutes of first opening the report.
The next morning, I had a little time to poke around before a meeting, and I looked at the incident database in the github “Veris” repository. It contained over 1000 individual files, each representing a particular incident for which they had publicly-releasable data. Far too much to review by hand. So I started sorting the data on individual fields. First, I tried URLs from each file, but there were still too many to look at. I also tried searching for likely words, hints, things like pastebin, but still there was too much to process in the little time I had.
Then I saw a tweet from another Dark Lord of the Sith (@darthmdh - Matthew Hawkins), who said “So I’ve made it to ‘Johnson Packaging’, that wasn’t so hard! #DBIRpuzzle” Bingo! That’s the one. Turns out, he simply searched for the hash value found in the beginning of the doc, and there it was. (In fact, that was the sole purpose of that hash, which I’ve been told was just an MD5 hash of a throwaway text like “this is the text for the marker” or something. Sad, I was hoping it’d be “O HAI HASHCAT”).
Also, it turns out that what I could have done was to sort by the master_id. All of the IDs in the file included “osint” except for one: CC2013 (“Cover Challenge 2013”). That one should have been easy to spot. The incident file contained several clues to lead one to Pastebin, to look for a data dump from the “Case of the Mondays Hacker Troupe” (cotMHT).
This dump file contained 5 password hashes, some silly hacker-esque stuff, and a funny ascii logo. The hashes (4 of which were named after Jackson 5 members) decoded to lyrics from “ABC”: Michael / abc, Tito / easy, Jackie / as, Jermaine / 123, and Danzig / iiiiiiiiiiiiiiiiiiii. So…nothing helpful here either.
At that point, I had to get on a train for a meeting downtown, but I was able to do some digging while en route. The “silly hacker” commentary spoke of “epic ukulele solos on the Tube of You”, which, of course, I’d LOVE to watch that while on a crowded subway train. As it turns out, there wasn’t any real content in they lyrics (that’s okay, there probably wasn’t much real content in the song they were parodying either). All the important bits were on the whiteboard in the background.
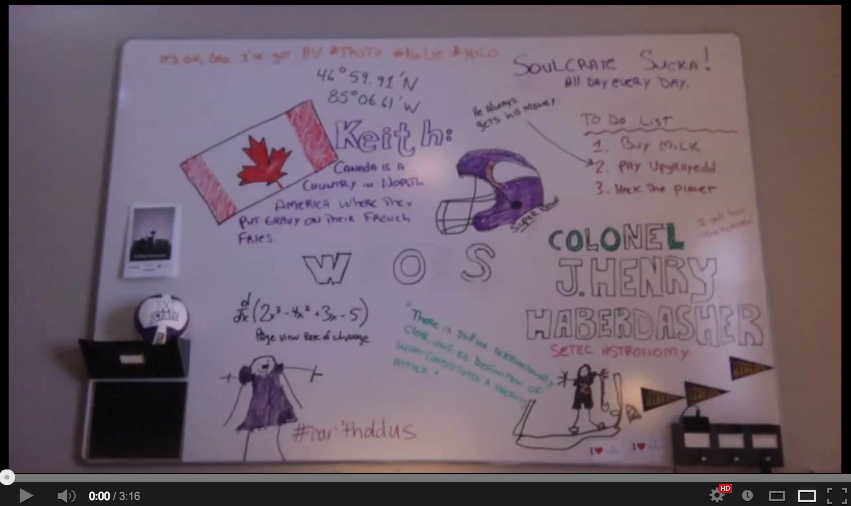
Prominent bits on the whiteboard included:
- The latitude and longitude of the site of the Wreck of the Edmund Fitzgerald (/me cues up Gordon Lightfoot)
- A large Canadian flag, and other references to Canada
- A quote from the Chinese MoD in response to the Mandiant APT report
- Setec Astronomy
- Colonel J. Henry Haberdasher
At this point, I had arrived at my lunch meeting, and had to put the iPad away. But shortly after returning to the train (and viewing a tweeted hint: “The Colonel has been busier over the past month”) I searched for the right phrase and found the next stage of the puzzle.
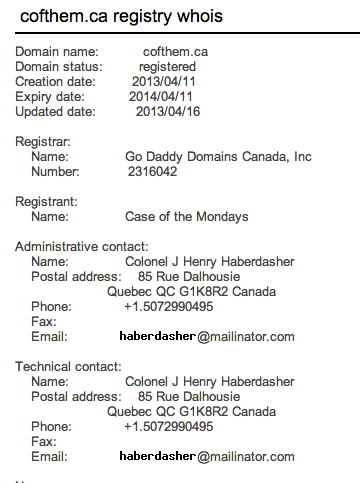
The phone number and address didn’t help any (the address is for the Museum of Civilization in Quebec – another Canadian reference), but the site that was registered certainly did: cofthem.ca (again, Case of the Mondays). But there was nothing at the site…just a blank, default “instant site” from GoDaddy. I tried several logins for the owner login panel (names and passwords from the Jackson 5 dump, for example) but eventually decided that it was the actual, legit GoDaddy site management panel and left it alone. I couldn’t view source on the iPad, so I tried several other “obvious” page names, like the unknown hash from before and other words, but found nothing.
I finally returned home, did some work stuff, and quickly decoded a hidden message on the pastebin dump (numbers hidden in the cotMHT logo spelled out “DRINK MORE OVALTINE”), then I dropped the kids off at an evening class and retreated to Panera for a bit. Shortly after sitting down, I looked at the YouTube page again. The ukulele video was posted by “Imstilla Hentz,” obviously a made-up name, but I couldn’t find anything else there, other than a default Google+ account. At this point, I even made a note in my log to check out other social networking / blog sites (I had in mind last year’s use of Pinterest) but didn’t pursue that any further. More on how that cost me first place in a bit.
After some time spent regrouping, trying to figure out just where I was and what I needed to do next, I looked a little more into how the “Instant Site” feature works. Turns out, it can only be used to create single-page sites. So there were no other URLs that one could read at that site, where the next clue might be. Back to square one for cofthem.ca.
After dinner and the kids’ bedtime, I focused on the supporting files for the Colonel’s website (all the while, @VZDBIR was telling us to search for what he’s been up to…which drove me buggy, as this was all I could find….) The javascript and CSS files all seemed to be the stock templates, the background image exactly matched one I found on another site, etc. I just couldn’t find anything at all.
Then, finally, a little before 11:00 pm on Wednesday, I realized that there was another item from the whois page I hadn’t searched for: The email address “haberdasher@mailinator.com”. Interestingly, Google didn’t give me much for that at all, until I tried searching on a 30-day window (which the hints had been telling us to do), and then I found two hits: One for a userid and password in the bugmenot database (which didn’t work on cofthem.ca), and another in “Hank’s Corner,” at “reallyclosetotheend.blogspot.com.”
Two minutes later, I noticed that this page had been created by “Ima Hintz,” the fictitious user from last year’s puzzle. And it was even available on Ima’s blogspot profile page. Which still contained links to last year’s Cupcake and ASCII Art pages. And the YouTube user “Imstilla Hentz” was, clearly, meant to evoke “Ima Hintz” from last year. If I’d thought that through a bit more while at Panera, I would’ve found this final stage 6 1/2 hours earlier than I did, and probably would have had the puzzle won by 7:00. Blast. Even crazier, if I’d decided to spend some time Monday night reviewing how things worked last year…and visited Ima’s page..I might even have found the puzzle within hours of the report’s release. I’m convinced the Verizon team did this deliberately, just to annoy us. Sneaky, sneaky, you magnificent bastards.
Fortunately, I knew exactly what to do with this puzzle, as earlier in the day my brother had sent me a link to the “Haberdasher’s Puzzle” (incidentally created by someone named Henry). Once the pieces were rearranged in the correct manner, the ciphertext would be readable, and I could proceed.
I took a short break to get prepped for bed (I was dead tired by now) but wanted to keep on until I was done, or fell asleep in my chair. Being so tired made getting the pieces lined up exactly right was difficult. Fortunately, a clear pattern was easy to discern – the numbers went “A, B, C, D-E” over and over. By making sure that I preserved that pattern as I read out the ciphertext, I eventually had a nice file with all the right numbers in the right places.
I quickly surmised that this was a book cipher (like had been used in the 2011 DBIR challenge), but which report is it built against? The “-” in the ciphertext broke the numbers up into 5-element groups, the first of which was probably the page number. Given that information, two of the reports were too short, so I first tried the current report. The first three letters were “EMA,” but the fourth one was broken: “16,26,5,6” didn’t work – there weren’t 26 paragraphs (the 2nd number) on page 16. I glanced at the 2010-2012 reports, they weren’t any better, so I skipped this and tried the next, which was “L,” so this was probably “EMAIL”. (looking back now, I see that a comma got dropped, and I should’ve noticed that “16,26,5,6” really should have been “16,2,6,5,6” and the missing “I” would have been right where I expected it).
Though the final message was clear pretty quickly, I kept on decoding right to the final character, and only then did I send the email. The message read:
EMAIL BOOK CIPHER AGAIN? TO DBIR AT VERIZON DOT COM
Which I did. Then I checked Twitter. And saw that someone else had won almost exactly an hour before me. Arrrgh!!
Still, though I didn’t win first prize, it was a fun puzzle, as expected. As I said earlier, this one felt a little different, with very little real cryptography or even puzzle solving, and a lot of finding exactly the right hint at the right time. It definitely needed a different mindset to attack, and I think that hurt me a bit, especially when I found myself mired in stego and website tarpits. Keeping an open mind and regularly stepping back to look at the big picture was key to finishing this challenge.
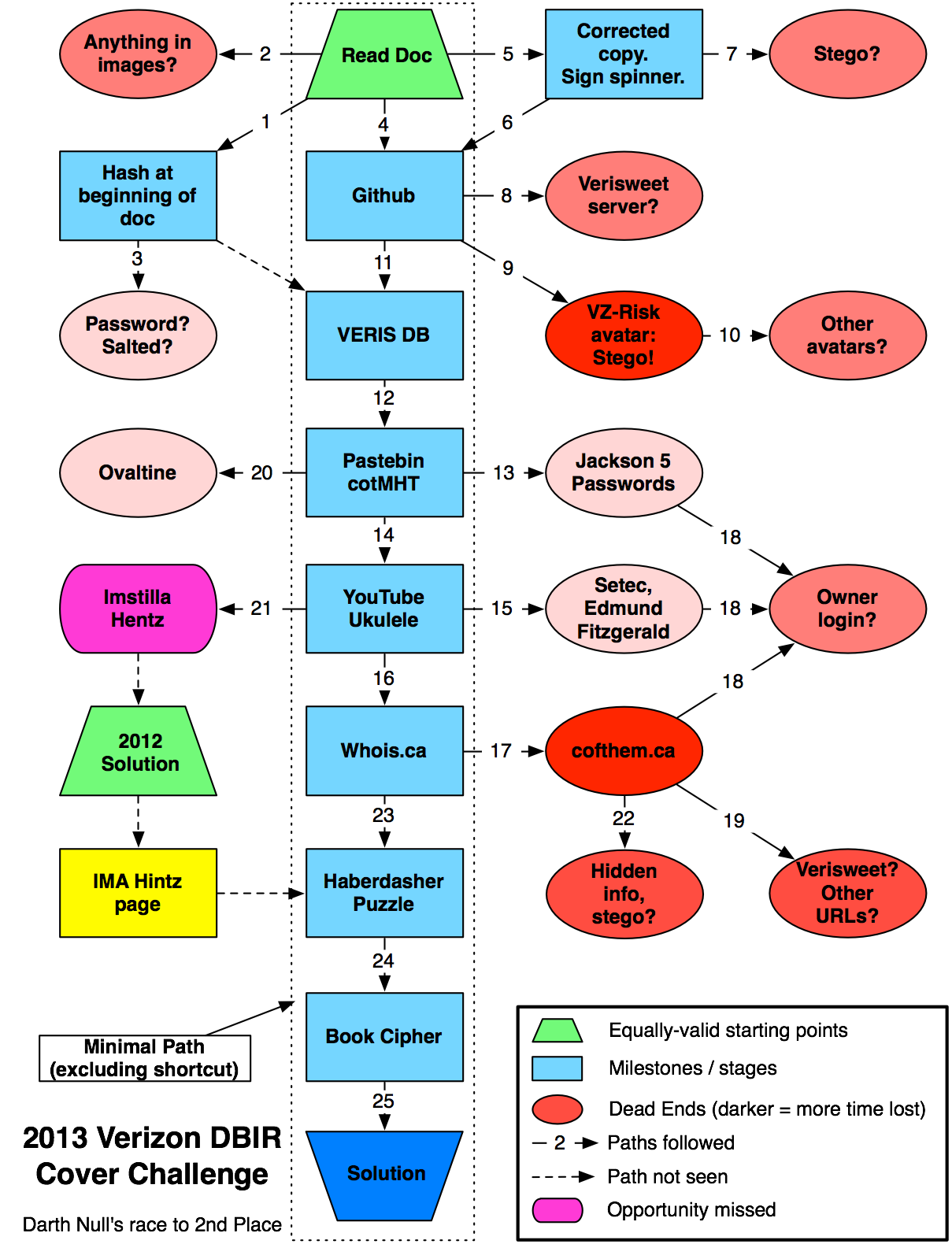
For fun, I created a flowchart showing the circuitous path I took to complete this puzzle. It’s especially frustrating to see all the dead ends I visited, compared with the “ideal” path straight down the middle. Even more so when I see visually described the opportunity I missed near the end, and most especially when I think about the “Just skip past the entire puzzle and jump straight to the last stage” troll via last year’s Ima Hintz blogger account.
Congratulations go out to Mike Czumak (@SecuritySift, twice before a DBIR Honorable Mention finisher) and his teammates @Blackjack988 and @LaughingWill. They’ve posted a great writeup themeselves, and it’s definitely worth a read.
I’ll get you next year.
(view Archived Comments from the old site)

