2012 Verizon DBIR Cover Challenge

DBIR Cover
Every year, the Verizon Business Risk Team publishes a Data Breach Investigations Report (DBIR), analyzing trends and other great statistical information gathered from working hundreds of different, well, data breaches. For the past few years, the report has included a puzzle / challenge / crypto contest. I heard about the 2009 puzzle too late to play, gave up in disgust trying the 2010 puzzle, and skipped the 2011 puzzle (‘cause I was actually working another puzzle at the time). This year’s report came out a few days ago, and I immediately launched into trying to solve it. It took a few days, but I managed to not only solve the challenge, but I came in first! Of course, as I’m prone to do, for every little step I took forward I first took about three giant steps sideways (often repeated in two or three different directions.)
As always, if you’d like to try to solve this yourself, then STOP now, as the rest of this post is full of spoilers. If you’d like to see just what you need to complete the puzzle, with no spoilers, click here: Verizon 2012 DBIR Sources.
Where do we begin? Looking at the cover, I see some interesting things…but nothing that I can work with right away. In past years, there was a big block of encrypted text hidden in the PDF, so I pull out some tools and find that (actually, simply a select-all and copy would also find it, hidden behind the image on the front cover).
VGhhbmsgeW91IGZvciBwYXJ0aWNpcGF0aW5nIGluIHRoZSAyMDEyIFZlcml6b24gREJJUiBDb3Zl
ciBDaGFsbGVuZ2UuCldlIGhvcGUgeW91IGVuam95IHRoaXMgY2hhbGxlbmdlIGFzIG11Y2ggYXMg
d2UgaGF2ZSBlbmpveWVkIGNyZWF0aW5nIGl0LiAgCgoKVGhlcmUgb25jZSB3YXMgYSBsYWR5IGZy
b20gTmFudHVja2V0LApXaXRoIHRleHQgc28gd2lkZSB3ZSBjb3VsZCBncm9rIGl0Lgp3ZSBjaG9w
cGVkIGFuZCBzbGljZWQgaXQgYWxsIGRheSBsb25nLApPbmx5IHRvIGZpbmQgc2hlIHdhc27igJl0
IGFsbCB3cm9uZy4KCldpdGggc2tpbGwgYW5kIGVhc2Ugd2UgYmF0dGxlZCB0aGlzIGZpZ2h0LApF
eGNlcHQgc2hlIHdhcyBub3QgdG90YWxseSByaWdodC4KVHdpc3RpbmcgYW5kIHR1cm5pbmcgd2Ug
a2VwdCBvbiBzdHJvbmcsCldlIHNob3VsZCBoYXZlIGJlZW4gc2luZ2luZyBhbGwgYWxvbmc6CgpN
YXJ5IGhhZCBhIGxpdHRsZSBsYW1iLApsaXR0bGUgbGFtYiwgbGl0dGxlIGxhbWIsCk1hcnkgaGFk
IGEgbGl0dGxlIGxhbWIsCndob3NlIGZsZWVjZSB3YXMgd2hpdGUgYXMgc25vdy4KCkFuZCBldmVy
eXdoZXJlIHRoYXQgTWFyeSB3ZW50LApNYXJ5IHdlbnQsIE1hcnkgd2VudCwKYW5kIGV2ZXJ5d2hl
cmUgdGhhdCBNYXJ5IHdlbnQsCnRoZSBsYW1iIHdhcyBzdXJlIHRvIGdvLgoKSXQgZm9sbG93ZWQg
aGVyIHRvIHNjaG9vbCBvbmUgZGF5CnNjaG9vbCBvbmUgZGF5LCBzY2hvb2wgb25lIGRheSwKSXQg
Zm9sbG93ZWQgaGVyIHRvIHNjaG9vbCBvbmUgZGF5LAp3aGljaCB3YXMgYWdhaW5zdCB0aGUgcnVs
ZXMuCgpJdCBtYWRlIHRoZSBjaGlsZHJlbiBsYXVnaCBhbmQgcGxheSwKbGF1Z2ggYW5kIHBsYXks
IGxhdWdoIGFuZCBwbGF5LAppdCBtYWRlIHRoZSBjaGlsZHJlbiBsYXVnaCBhbmQgcGxheQp0byBz
ZWUgYSBsYW1iIGF0IHNjaG9vbC4KCkFuZCBzbyB0aGUgdGVhY2hlciB0dXJuZWQgaXQgb3V0LAp0
dXJuZWQgaXQgb3V0LCB0dXJuZWQgaXQgb3V0LApBbmQgc28gdGhlIHRlYWNoZXIgdHVybmVkIGl0
IG91dCwKYnV0IHN0aWxsIGl0IGxpbmdlcmVkIG5lYXIsCgpBbmQgd2FpdGVkIHBhdGllbnRseSBh
Ym91dCwKcGF0aWVudGx5IGFib3V0LCBwYXRpZW50bHkgYWJvdXQsCkFuZCB3OGVkIHBhdGllbnRs
eSBhYm91dAp0aWxsIE1hcnkgZGlkIGFwcGVhci4KCiJXaHkgZG9lcyB0aGUgbGFtYiBsb3ZlIE1h
cnkgc28/IgpMb3ZlIE1hcnkgc28/IExvdmUgTWFyeSBzbz8KIldoeSBkb2VzIHRoZSBsYW1iIGxv
dmUgTWFyeSBzbywiCnRoZSBlYWdlciBjaGlsZHJlbiBjcnkuCgoiV2h5LCBNYXJ5IGxvdmVzIHRo
ZSBsYW1iLCB5b3Uga25vdy4iClRoZSBsYW1iLCB5b3Uga25vdywgdGhlIGxhbWIsIHlvdSBrbm93
LAoiV2h5LCBNYXJ5IGxvdmVzIHRoZSBsYW1iLCB5b3Uga25vdywiCnRoZSB0ZWFjaGVyIGRpZCBy
ZXBseS4KJHAK
This text decoded, not to an encrypted binary, but to a poem:
Thank you for participating in the 2012 Verizon DBIR Cover Challenge.
We hope you enjoy this challenge as much as we have enjoyed creating it.
There once was a lady from Nantucket,
With text so wide we could grok it.
we chopped and sliced it all day long,
Only to find she wasn’t all wrong.
With skill and ease we battled this fight,
Except she was not totally right.
Twisting and turning we kept on strong,
We should have been singing all along:
Mary had a little lamb,
little lamb, little lamb,
Mary had a little lamb,
whose fleece was white as snow.
And everywhere that Mary went,
Mary went, Mary went,
and everywhere that Mary went,
the lamb was sure to go.
It followed her to school one day
school one day, school one day,
It followed her to school one day,
which was against the rules.
It made the children laugh and play,
laugh and play, laugh and play,
it made the children laugh and play
to see a lamb at school.
And so the teacher turned it out,
turned it out, turned it out,
And so the teacher turned it out,
but still it lingered near,
And waited patiently about,
patiently about, patiently about,
And w8ed patiently about
till Mary did appear.
"Why does the lamb love Mary so?"
Love Mary so? Love Mary so?
"Why does the lamb love Mary so,"
the eager children cry.
"Why, Mary loves the lamb, you know."
The lamb, you know, the lamb, you know,
"Why, Mary loves the lamb, you know,"
the teacher did reply.
$p
That’s neat. Now what?
Well, there are a bunch of numbers on the cover. There’s a 405 in ‘h4x0r5,’ and phone numbers on another sign. Though these phone numbers are incomplete, and don’t even seem to have a real area code. Maybe I need to use those numbers as an index into the poem – like find the 405th character, the 696th character, etc. If I include the stray “8” in the poem (“and w8ed patiently about”), then I’d have enough for a 5-letter string, maybe as a code at a URL shortener.
But none of this worked, and after a day or so of playing with this a little, a hint was given on Friday night that told us “If you found Mary, you’ve gone too far.” So the whole poem might even be a red herring. This means I don’t have much at all to work with. Just the numbers. And the cover.
Saturday morning, I played a little looking for steganography (looking at the lowest bit, and also treating the three numbers in the phone number as an RGB triplet to search the image for), but gave up on that pretty quickly. Maybe I can get an IP address out of the numbers. I tried factoring the numbers but found nothing obvious. I tried treating it as a single number and converting that to a dotted-quad internet address. That didn’t work. I even tried dropping the first or last number to treat them like hex (0x69651321) but again, no luck.
Finally, I tried 69.65.13.21 (this made some sense, since one copy of the number was torn off leaving only the last digit behind), and found a website that looked promising: An unconfigured Wordpress blog, but after several minutes of explorign I didn’t find anything useful there. Then I realized, wait, I haven’t tried 69.65.13.216 yet. Trying that got me “Server 1 online.” I then tried that on port 443, and got a certificate mismatch error – telling me that I was trying to connect to pastebin.com.
Alrighty, then! Pastebin! But what paste?
I tried searching for different strings from the signs on the cover, and for things like DBIR and Verizon, but had no luck. Finally, I hit paydirt with “half million personal” – and got a huge list of hashes. There were over 14,000 of them…but as I looked closely, I noticed that one of the hashes was short (the last digit had been dropped). Then I saw that a lot of them ended with the same numbers (which told me they were probably LANMAN hashes), and looking even further, saw there were a lot of full-on duplicates. After passing the list through a couple of awk and sort | uniq -c steps, I found that one hash, and one hash alone, was unique in the entire file.
imahintz@gmail.com,98B451441C75C9F0F3BD49EDF32EB4A4
It only took another minute to lookup that hash online, and found that the password was “PINTEREST.” Cool! So I dashed off to Pinterest and looked for the name associated with that hash, which was “imahintz” (which, obviously, would’ve been a good clue if I’d taken the time to look at all 14,000+ emails).
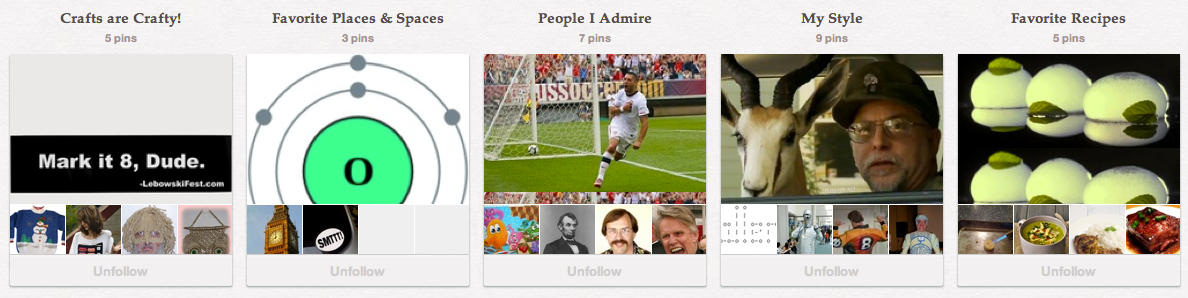
The Ima Hintz user had five pin boards: Crafts, Favorite Places, People, My Style, and Recipes. Right off, the Style board catches my attention because of a picture of Chuck Testa, subject of a recent viral Internet meme and mentioned directly in the DBIR. Most of the rest of them just look like silly pictures to help fill out the account. Looking at the activity history, the most recent items to be pinned were four people (Larry Wall, a soccer player, Q-Bert, and Lincoln), then Chuck Testa, something about Oxygen, a couple of recipes (Mojito foam and Cupcakes), and finally, an image of ASCII art spelling “Challenge.” So let’s look at that last one!
That takes me to a blog, where I see the Challenge image (ironically, not even ASCII at all but a .png image), and some DBIR logos, and a big present made out of base-64 looking code, complete with a ribbon and bow. Decoding the base-64 (which I note has only lowercase letters) gives me a big chunk of binary, which I assume must be the ciphertext. I tried a bunch of keys (variants of phrases associated with Chuck Testa, also stuff from other images on the Pinterest account, like Puddy’s Eight-Ball jacket, etc.), not really expecting it to be that easy. It wasn’t.
***
**** ** **
** *** *** ***
*** *** ** ***
*** *** ***
*** * ***
*** * ***
******
8vvpojkjq3c8a7d0ryi5fghqc9wvi7zba0puzyk**az3tkq5jdof2ssdcca01r0epgxu2sgvb2uz
jx5l7xxm0a11i5nsyhjkor8xe9ae06k27sumhqi**8qhrb1x7kixt53p5etuktrj35b9brrbnvtc
c24njbtr2jz1zjkc785ns1of43i7abcbkylsunp**soekn22c8r5asmbxd6opnfp5xk113hrca3m
kbubf9t1clswoqqucq7lke9inokuz3l46eu1tgq**q4gk1en3t1qmp2gzmc679x03t9y5x709cq5
obmzdh35v0rkq6oyk67d4jsgo08rco5yoji90mv**fbs1ye1rzjkm75l02zyb7vi1mxt1rkr3ba2
d6gkr2mc5lrsipbeboggz2415q7b01o1khy0zn8**rhxlq33k40lsm0nttyr88oiqtz8r1qtnexr
4t688b1cm8q2d2id7jufvuzy6g48bbyej9grqdy**d8yb5wl8kqc9nbb6ldhzn0suj3br59u74ft
lf8c3ea675n31b6qwnmej5hwv48teo86056tw35**i7o7l64uoa2evkyk1yuprjfyjirhny5ubpv
bnhcwn5hwmp0kxcgbw5b2w4l6oaojpz182j7ywt**ampoqhfxsy9x71wxjvgdq1cy09z15z2lii0
rcobyczafy5ltupcavoipmcjxh6h9mj6ok6xdsj**v4atn4ips2xc2rzauv4e9i0hyo7ay4k18cx
ij2hid3mdfhd74qkbz06nk066w6scml2efuhgsp**mlh7h8i36u5he05aajk2p4939jf7x1gejmv
qmsicuyxcen6ieav2acr5bs947c1y759sbbq3ws**r7hig36yv5v93qqpx9pr6j9g3esiatg3hue
****************************************************************************
ltvm632gqf31bhykk0wokp6jmkn5idji62r6id1**f4ncrulceizzc23p95rs1sdby5hyrnkcvku
2ehd4wrr629xsvpmivr3rc0b37907e4emlbrnbe**i0iyuhrmull00poau4hip6tefqx4v93q2js
r5mgcndutkxlk24ytxuxtgbzlhplmemdm7cj2gj**vwahybu5safhha9thsnxmk0jf71jc3zityg
cqk22nw1otk2fvxvzk1lglybb3xldpmphqrep2a**qpdjbomyres6n4tun2lyjmzdvpxjjty36gk
2gg42qtiykehb46dqgvi37gyv41ddtd110oh3m3**ub559tyxcqbvns5c0ts2lsitkhwrhim9pt5
pi47v37gh2vl34x0257mdmbb9pijcxgxkvxfiwc**2qxrmwe4ypfatf095gvqv6j5snavdnpcjj6
jowfuky2xlagtg27lhg951j70esmd2coj649k56**aiikyzzitx1ryjpuxxhkdi2j0xswamim469
3z4ojtkh7dkoguwy5c4z47y1fdbayle2cjs9lv9**vj0h0oovwe3uoli3uypekb7aa9irfmhjuqr
u3j7m5giarcyd7b92rdv1ec0ov47bvqgm6228dp**jzz8jurl617zch0yz2ld0ft3r9k97g0lk2d
du8vdfu2wlop1qb2h9fwg5xdeod77aythvpvvyy**vqfeu679095is2ps6kfgehoerrv60ytanv0
wvnojkezih25kr1sn30cv4sifxjaxpgkmfohwdw**zjvtmpp4vs45fuds061rdcg4n6q3kpnhf8k
6bdq98gv0p372n4butt5gn7s63ek8jct5zkx49d**yj1ycg0knp0uvmpke6yio32sx89m2qnjeo6
v0uygrre88nz
Then I noticed that the cupcake recipe is called “Encryption Cupcake Recipe.” Cool! The recipe has little bits that can help, like -nosalt and “a pinch of OpenSSL” but not much more. And I’d already assumed the -nosalt based on the ciphertext I was working with. I also checked the original recipe that this one credited, and saw that they’d added caramelized bananas, but didn’t think that was significant.
All along, I’ve been keeping @wadebaker informed of my progress (he’s a member of the DBIR team, and seemed to be tweeting the most about the contest). I mentioned that I was thinking the key might be in one of the password hashes, and he told me “I think u prolly got all u needed from that step.” Because I was addled, or hungry, or just stupid, I read that as “Good idea, you have all you need to make that happen.” What he meant, I learned a couple hours and 99% of the passwords later, was “No, you’re done with that step, move on.” D’oh.
So I’m back to looking at “the gift.” Interestingly, it’s almost the same size and shape as the base-64 code that gave us the opening poem – a couple characters too narrow, and a line too short. It’s also all lowercase, which I belatedly realize would be next to impossible to force if you’re encoding a random binary file (which an AES ciphertext would closely resemble). No idea why I didn’t think of that before. So maybe it’s uuencoded, not base-64? No, that has the same problems. Maybe the whole thing is base-36? But how would you convert that back to 8-bit binary? You’d need, maybe, to have two-character pairs (essentially, base-676 digraphs) and as long as no digraph ever reached 512, that’d be a 9-bit value represented by each digraph. String enough of those together, divide into 8-bit chunks, and you’ve got output. Voila! Except…well…that’s a bit crazy, even for me.
After telling Wade all this (and admitting how far afield I’m drifting) he suggests that this step might be “more puzzle than crypto.” So, okay, regroup, and revisit the original poem. It mentioned slicing and chopping, twisting and turning – maybe this is a big transposition cipher, and I need to shift rows around and such. But that seems almost as complicated as my base-676 craziness, and I don’t think much about it. Well, let’s fall back to looking for something hidden behind the text, and look at the HTML source for the gift image.
Interestingly enough, it’s all broken up. There’s an 8, then a bunch of characters in a single SPAN tag, then another 8, then another SPAN of other characters, then another 8…. Not wanting to jump to conclusions, I painstakingly check every single row in the image and, sure enough, every single 8 is separated out from the other characters. There’s something special about the 8s. Which I should have noticed earlier – a bunch of the pictures on the Pinterest site had prominent 8s, the poem had an 8 in ‘w8ed’, and even a couple of the hints on twitter had used 8 (like “devest8”).
8..........8................................................................
......................8..................8..................................
.................8...............................8..........................
............................................................................
..........................8.................................................
......................................8.....................88.....8........
...88....8.................8..............8.....8...........................
..8.......................8...8.............................................
................................8...........................................
.........................................................................8..
..............................................8.............................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
............................................................................
....................................8.......8...............................
..8.........................................................................
..........................................................................8.
.....8......................8.....................................8.........
........88..
Also, the report itself mentioned that they’ve been producing the DBIR for, wait for it, eight years. Another interesting thing, is that when I hide all the other characters (turning them just to dots), there’s a big multi-line gap about 2/3 of the way down without a single 8 in it. None of the other characters show this – they’ve all got more normal looking distributions. Again, clearly, there’s something special about the 8s. But what?
Crazy Eights
I tried resizing the array of characters, thinking that maybe it’s supposed to turn into a picture. Or maybe if I resize it to 8 rows, it’ll be like 8-bit-wide paper tape. Or maybe it’s Morse code. But ultimately, there’s just not enough information there. There are only 32 of the 8s, that’s just not enough to convey anything useful, at least not as bits. But perhaps it’s the spaces between the 8s that matter – and I count them out and convert them to letters, but again, this gives me nothing, even when I try various Caesar shifts on the output. So…Saturday ends with me having made some good progress, but still feeling quite stuck.
I get back at it first thing Sunday morning (after the kids have dragged me out of bed to investigate a robin that’s been attacking its reflection in our dining room window). The ribbon on the gift looks almost like axes on a graph, but I can’t think of how to use that. With nothing else to go on, I tried playing with some of the other images I’d seen – cupcake pictures, etc. – looking for more stego, using the tool they used last year. Then I get a note from Wade: “What does Mary live in?” I immediately think of the original base-64 text from the report cover, and instantly I know what the trick is: A grille cipher. And I realize that I’d, again, been shortsighted: removing the ribbon (as I thought the stars that made it up were just window-dressing) resulted in a gift image that was smaller than the base-64 text that produced the poem. But leaving it in place meant the gift was exactly the same size. Which absolutely should have been something I paid more attention to.
Fifteen minutes later, I’ve written a script to simulate the grille: it converted both the gift and base-64 text to long strings, and counted forward in the grille string. Whenever I encountered an ‘8’ in the first, I output the corresponding character in the second.
Another way to imagine this is to simply layer lines one atop the other:
8..........8................................................................
ciBDaGFsbGVuZ2UuCldlIGhvcGUgeW91IGVuam95IHRoaXMgY2hhbGxlbmdlIGFzIG11Y2ggYXMg
......................8..................8..................................
This gave me a base-64 string:
V1hHWmxVaGplc204cVNVam1TbU92ZVJH
Which, when decoded, gave another base-64 string:
WXGZlUhjesm8qSUjmSmOveRG
Just like it’s pretty much impossible to make a random binary encode to an all-lowercase base-64 text, it’s very unlikely that a random base-64 text will decode to another valid base-64 text. So I take this as an indicator that I’ve finished this stage successfully, and go make breakfast. While eating (“Daddy, why do you have your computer at the table?”) I look around the Pinterest page again for other ideas on keys.
Where’s the Key?

Cipher
Two years, ago, the key was a phrase that you had to find on the web. Last year, they made it somewhat more explicit and had the key hidden as stego text inside an image. So this year, I was looking for something equally clear (and hopefully directly visible). I revisited the script I (unsuccessfully) used in 2010, and added things like “nope! Chuck Testa” (referred to in the DBIR text), “All signs point to ‘Yes!’” (from the page describing Puddy’s Eight-Ball jacket), and several other variants and other phrases and words. All with different uppercase and lowercase and punctuation permutations. None of them worked.

Mark It Dude
Then I realized I was just spinning my wheels (and was feeling stressed ‘cause I just knew someone else must be about to beat me to it). So I stepped back and looked around a little more…and looked more closely at the cupcake recipe. The only thing that was changed from the original recipe was the addition of the bananas. I looked, again, very closely at the image of the torch on the banana slice, and saw nothing. I also looked closely, perhaps for the first time, at the picture of all the cupcakes, and noticed “-base64” written next to one of the banana slices. Superimposed on another was “-rc4-40.” Aha! So now I know exactly what cipher to use (and it wasn’t one I’d been testing against). Updated my script, ran the keylist through again, but still, nothing.
Stepping back for a moment was so helpful that I did it again, and sat staring at Ima Hintz’ home page for a little bit. Wait – there’s an 8 I totally missed. It looks like a bumper sticker, with “Mark it 8, Dude.” on it. I opened up that pinboard, and that image was one of only a few with a caption: “Markitdude.” (was this a pun, to refer to the “marketing dudes” who probably end up paying for the contest prizes?) I added both of those to my list, ran it, and…success!
**** DINGDINGDING ****
Password: Markitdude
Output: email 8trak 2dbir
At 11:40 am on Sunday, after half-hearted poking around on Thursday and Friday and a nearly all-day bender on Saturday, I’ve solved the puzzle.
I immediately sent off a DM to Wade, and followed up with an email to the dbir email address sprinkled throughout the DBIR text. Then I went to my mother-in-law’s house to help with some light fixtures (but I brought my laptop with me, just in case). And waited. And waited. Finally, about 3:00, I heard back – I’d won! Woohoo!
Too Long; Didn’t Read
(Yes, I know that’s supposed to go at the top, so you don’t have to read all the rest of this. Tough.)
- Find the base-64 text hidden on the front cover. Don’t bother decoding, the content is a red herring. But do add some newlines so it looks all nice and pretty.
- Convert the incomplete phone number (696) 513-216 to the IP address 69.65.13.216, and go there using HTTPS to get redirected to pastebin.com.
- Enter the text from the sign which had the phone numbers (“half million personal records”) to get a password dump.
- Realize that the dump is full of duplicates, but also includes a single unique hash.
- Crack that hash to get pointed to pinterest.com, and use the email address for that hash to get the Pinterest user’s ID.
- Find the Challenge picture on the Pinterest site and, clicking on it, find the ASCII “gift” image.
- Realize the importance of 8s (by viewing source on the gift image, or by noticing all the 8s in all the pictures, or by looking at the visual distribution of each character in the gift and seeing that 8 is “different” from all the rest).
- Realize that the gift, and the base-64 text from step 1, are exactly the same size and shape.
- Use the 8s as a grille cipher, and uncover the corresponding characters from the base-64 text.
- Decode that string to get another base-64 string. This is the final ciphertext.
- Find the “Encryption Cupcakes” recipe on the pinterest page and see the clues in the text and the picture: openssl, -nosalt, -base64, -rc4-40.
- Look around the pinterest site some more, and see the “Mark it 8, Dude.” picture, and realize that it’s only one of four pictures with a caption (another was the 3 Wolf Moon t-shirt from last year’s puzzle).
- Use that caption as the decryption key.
- Win.
For completness’ sake, here’s a command to perform the final decrypt (all one line):
echo 'WXGZlUhjesm8qSUjmSmOveRG' | openssl enc -d -rc4-40 -base64
-nosalt -pass pass:Markitdude
Conclusion
This was an excellent puzzle. It had lots of clear indicators of success, but also plenty of distractions. I spent some time searching for things like “wadebaker” and “pirogue” because of random, offhand tweets he’d made. There were lots of interesting looking comments around Figure 42. Chuck Testa satisfied the need for a meme, like last year’s puzzle. Not to mention the cryptic text in the initial red herring poem.
Ultimately, though, everything we needed to win was on some kind of page or document created or maintained by the DBIR team. Nothing came from any 3rd party page (no comments on YouTube videos, or in Amazon listings, or on the Puddy or Chuck Testa pages linked in Pinterest). All clearly marked, and very “conspicuous” (which was the twitter ID used for some of the hints, and the name of the user who posted the password dump). The big trick was simply noticing everything. And, as I’m sure was the case for many other players, I skipped right past most of the clues the first two or three or four times I looked.
It had a modern cipher (the RC4). It had a classic cipher (the grille), which was a little bit obscure, but I was actually thrilled to see it used. It wasn’t easy, but as usual, a large degree of the difficulty was simply My Own Fault, for missing things, or making stupid assumptions, or conveniently overlooking what should have been blazingly-bright red alarm lights that I was Doing It Wrong.
But as I completed each stage, the right answer was clear and hard to miss. The grille and original base-64 text being the same size. The 8s having a markedly different distribution. The base-64 text decoding to base-64. The final key being one of only four captions in the Pinterest account.
Bottom line: I absolutely loved this. Favorite part: The grille cipher, just because it’s a part of cryptographic history and I haven’t seen it used in a puzzle like this before (and it was used, I think, very well).
So, in the end, a big thanks to the DBIR team for a fantastic puzzle, an awesome prize (iPad!), and of course, thanks for the excellent Data Breach Investigation Report itself: for all the effort the whole team put into the collection and analysis of the data, and especially for making the report available to all the world for free.
Hopefully next year I won’t make as many mistakes.
(view Archived Comments from the old site)

