ToorCon 12 Badge Puzzle
In the middle of October, G. Mark Hardy emailed to ask if I or my puzzle-busting buddy would be making it to ToorCon, in San Diego, as he had a puzzle on which he was putting the finishing touches. I told him no, but that I’d love to play along at home for “bragging rights instead of prizes.”
The weekend of the conference I was actually at a cousin’s wedding. So I didn’t expect to have much time to play. However, I did bring along some gear, and spent some time Friday night and Saturday afternoon playing with the little information that had leaked out from the Con.
In particular, someone tweeted a very good picture of the badge. Unfortunately I forget who it was, and the picture isn’t showing up in a search any longer. But it was a great picture, and immediately got me thinking.
As always, if you’d like to try to solve this yourself, then STOP now, as the rest of this post is full of spoilers. If you’d like a copy of just the raw data (ciphertexts and other clues revealed during the contest), click here.

ToorCon 12 Badge
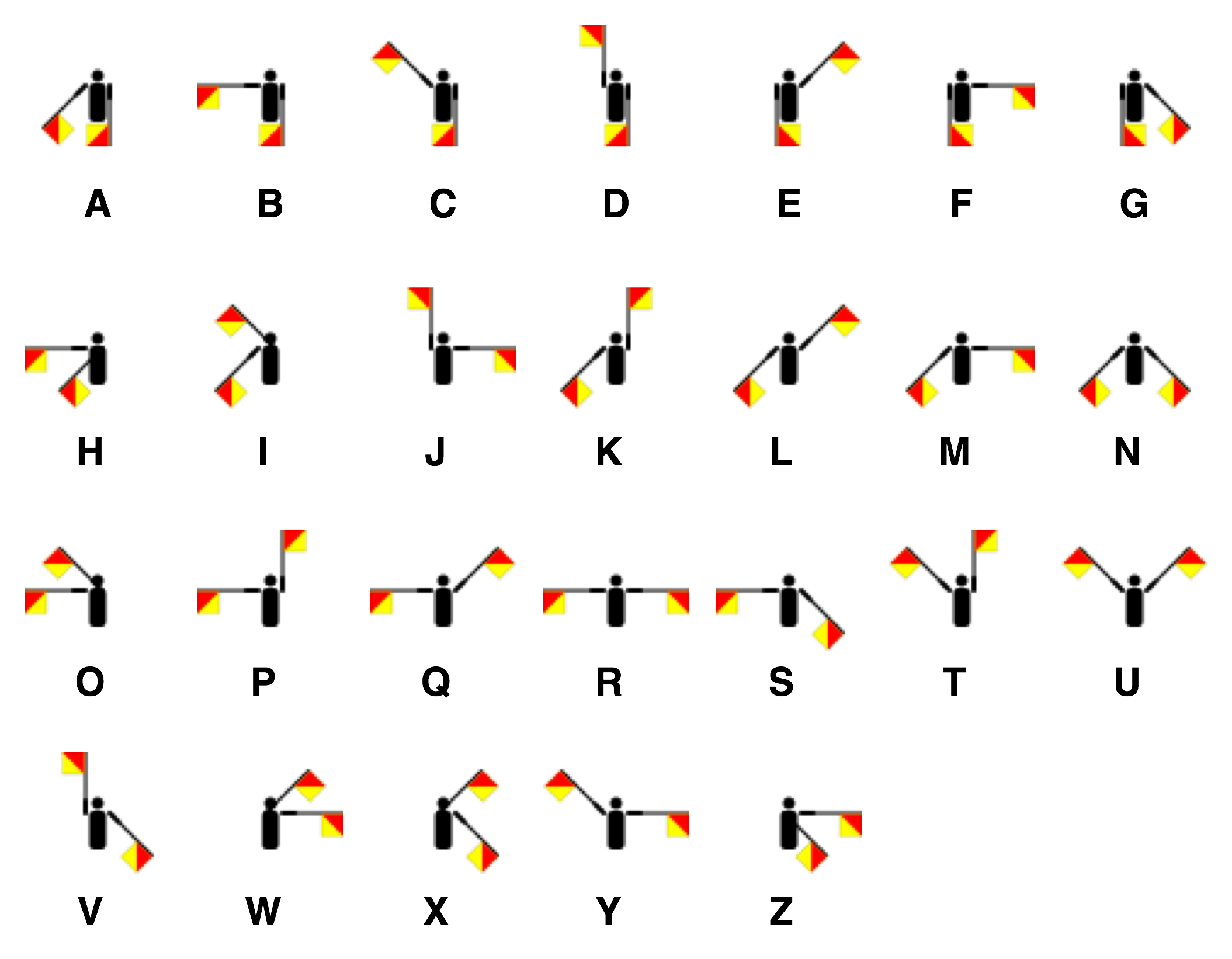
The times listed all around the perimeter of the badge really grabbed my attention right at the beginning. G. Mark was giving the keynote at the con, entitled “Pwning Time,” and so this was clearly part of the puzzle. He’s also had a history of using different symobologies in past puzzles – Naval signal flags at QuahogCon, and Morse Code and barcodes at ShmooCon. And knowing that he’s a retired Navy Captain – well, I almost immediately decided the times had to be Naval Semaphore code.
Unfortunately, a closer inspection showed that this would be problematic. Nearly half of the codes had the same “hour,” which seemed really unlikely for just about any simple substituion cipher. I played with the times for a while, trying all kinds of crazy sequences, counting tricks, etc., but just couldn’t get anything useful out of it. As it turns out, those were part of a totally different contest, and not even related to G. Mark’s puzzle.
About that time I also received word that there were multiple stages, requiring more than just the badge picture. The conference program apparently had several clues, and also a T-Shirt had some kind of ciphertext. So there was absolutely nothing I could do right away….which was good, since it was time to go to the wedding.
Of course, I still had my phone with me, and it buzzed multiple times that night and the next day with hints and information from @g_mark (all times given in Eastern, as that’s where I was):
10/23/2010 18:00 TOORCON crypto puzzle first hint - Start on the edge!
10/23/2010 20:33 TOORCON - I've asked if they would post images of badge, t-shirt, and program to website. Remember - start on the edge ... But of what? ;)
10/24/2010 13:40 TOORCON - Each crypto clue contains a riddle, a pointer to the next clue, and the encryption key. Follow the chain to the final answer.
10/24/2010 17:22 Your TOORCON badge is not a clock if you want to check the time. Could a clock face tell more than time? Could it send a signal?
10/24/2010 18:15 TOORCON if you have trouble getting started, .-.. --- --- -.- ..-. --- .-. -.-. --- -.. .
Interesting. So even in the middle of the afternoon on the last day of the con, he’s still giving pretty early hints. I wonder how many people were playing… And that definitely leaves the field wide open for me to snatch victory! :) Also, one of those clues (clock sending a signal) certainly reinforced my thoughts about semaphores.
Late Sunday night, I got some additional information from G. Mark, including a not-for-redistribution copy of the program and the text from the back of the con t-shirt (THANKS!!). So I sort of started my “official” clock at 11:00 that night. Not long after, I saw a final tweet:
10/24/2010 23:13 TOORCON thanks to players who purchased clues and raised $172 for Toorcon foundation. Farthest progress = stage 5 of 6. Thanks for pla ...
So people could BUY clues? Hm. New wrinkle. And still nobody solved it, although some people came close (though I wasn’t sure if this meant the farthest people were “at” stage 5, or had “solved” stage 5).
Anyway, I’m now looking through the program, and seeing clocks on nearly every page. With a different time displayed on each clock. And they’re analog clocks. So the hands really do look like semaphores. Always nice when a gut feeling turns out to be right.
However, his first hint said to “start at the edge,” and another tweet (in Morse code) said “LOOK FOR CODE.” So I pull myself away from the clocks and find some Morse code printed right on the edge of the last page (the dots were about cut in half – it bled right off the edge).
.-.. --- --- -.- .- - - .... . - .. -- . -....- .. - .----. ... .---- ...-- --- .----. -.-. .-.. --- -.-. -.-
Ah, that’s more like it. Pretty quickly I decoded “LOOK AT THE TIME” and moved on to the next phase, the clocks. Later, G. Mark mentioned something about “13 O’Clock” having confused some people, which in itself confused me – I had no idea what he was talking about. Then I realized – while reading the code, zoomed in on an iPad, I’d only seen (and decoded) the top half. I’d missed a whole half of the clue! The 2nd half was a hint that the text from the clocks was ROT-13 encrypted, which I’d sort of guessed automatically anyway. The full text from the Morse code was:
LOOK AT THE TIME - IT'S 13 O'CLOCK.
But I digress. The clocks, finally getting to try my semaphore idea. Using the Wikipedia page as a key, I converted the clock faces to text.
Clocks from Program Semaphores (adapted from Wikipedia)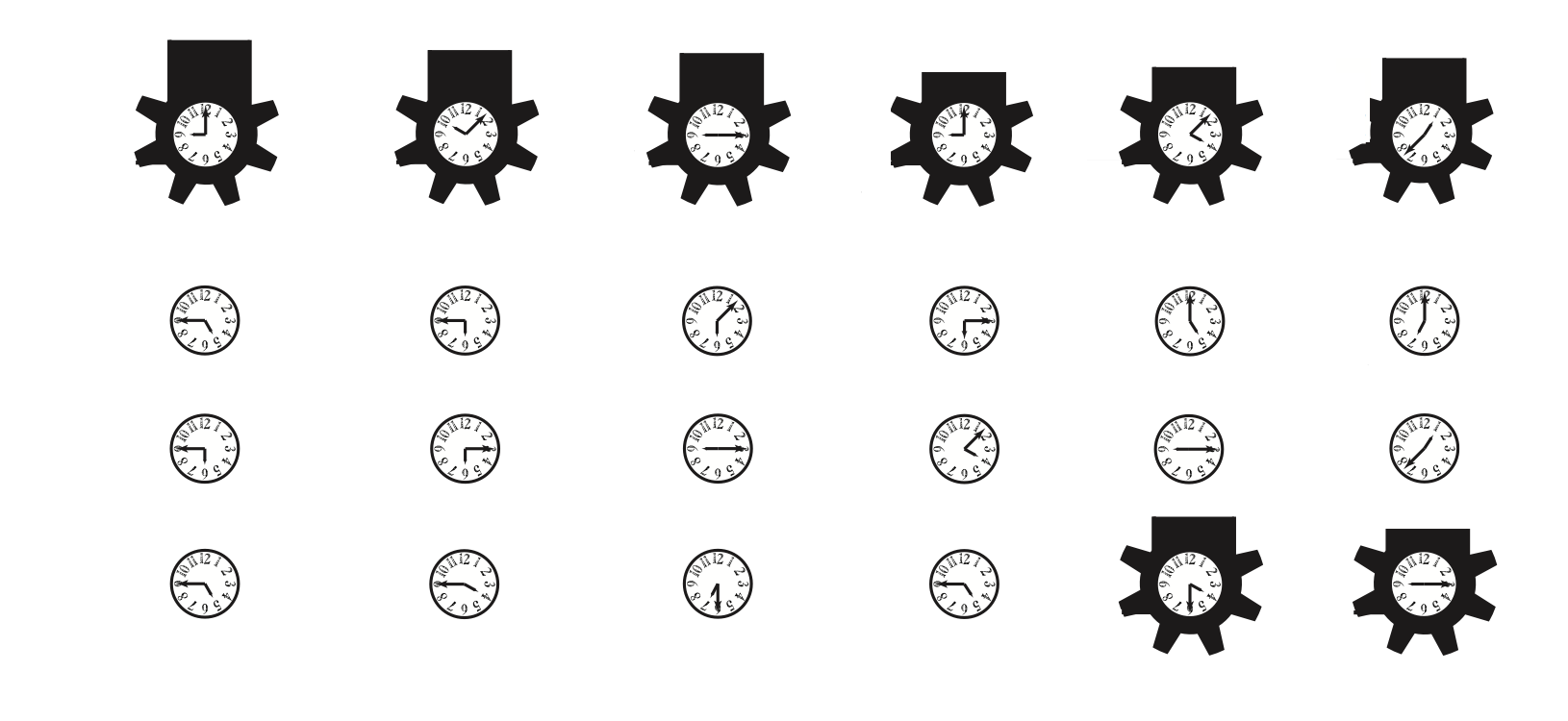
PURPXL SBEFVK BFRXRL SSASGR
which, ROT-13 decoded, gave me:
CHECKY FURSIX USEKEY FFNFTE
Obviously, there was something wrong, and I eventually decided that it was supposed to be:
CHECK YOUR SIX USE KEY OF NOTE
Apparently a few of the clocks got messed up when the program graphics were created. “Check your six” is military jargon. Six being short for 6 o’clock, which basically means behind or back. So “Check your six” is telling me to check my back. Back of the T-Shirt. So now I need the T-Shirt code, and use a key that’s somehow related to the keynote address. Here’s the ciphertext:
U FIDO YFAENY ETZVR
MT JZKQD FP RUGYD
YA UJO EAUI CQULC
DU SAZX OZSZQNF
LFYQ UNJSJQ
OW DNQ BRMQ OOMOX
IHVX EAU KBE
KOL GOXL USYOOMOX
ZEN CKORVDY EHFGKP
TYOXQ SFYT IICV HQ
IW IUG DVMUPE
NSZT KVI UR C
But what’s the key? It should be related to the Keynote, somehow. So I tried several words – KEYNOTE, TIME, PWNING, PWNINGTIME, GMARK, etc., and got nowhere. I also tried more direct attacks using online Vigenère apps, but also got nowhere. Because of a transcription error of my own, even after correcting the result of the clock phase I also got stuck down another blind alley for a bit. Finally, the next morning, I again tried the old standby – “GMARK.” Only instead of being a shift to Z as he’s used in the past (using Z as a space), it was a classicial Vigenère cipher. I know I tried that before, but must’ve messed something up. The result was:
O TIME STANDS STILL
AT SPEED OF LIGHT
SO USE YOUR SKILL
TO GAIN INSIGHT
LOOK INSIDE
OF THE BACK COVER
WHEN YOU TRY
YOU WILL DISCOVER
NEW SECRETS SHOWED
THERE SOON WILL BE
IF YOU DECODE
WITH KEY OF C
Now I’m getting somewhere. The inside back cover of the program had a big ciphertext string.
OCRUG HUCOW OUUGO WJZAN JYEQD KGHFO YSNNX RLARZ XTXOE CUPAL
OMTXL GAXZQ IAEKN TPVJH MNBTI YSWTB IOVCS KUKZH NHSQA PYFMZ
KOAQZ CHGJU OHUPV XBORZ AGZFD WHIJV WJDUB SEYON UQMYX FDOPS
RUFGC DNBUU MCHVD WTIVG ZUCSJ HCCUB NEAVE CBXSL IHZMX NQHBV
IKDJK VDDXK VEDSU CEJLN RMEAM
VHXWC ESQLP RNGBS DPRII ESBXR BXNZX AIGPR BEOWX SOLTG FTFUN
GEZMA MFCNG L
INCVI STYAL OVEMN SFXRW UEVJT VCGJA HSEMD ALPBF RONLO LWMAN
AXWVE WRLDT EZKNB UANAP GNHWA IWWBE BFTDJ OKCDX RYWTO QSBYO
OFEYS BIPNU XISXY WRDTI PJBMW OBRBW NCGVS AOBTZ LJBQT VSCBV
PJHEP LMLRV UXSHO MZTWO CPVOG SIHSL KVPCR YHPLD MOPOJ WWCNJ
NFTWO RQOWP HKAOZ IQDFA RBXFB VKXTK CPKQO YQIBU PZXSO LUWWC
AZHGB RLPCZ FPVEL HVQDH LQJTE DUNUX MRIRL PKJUB ESGAF CBAOF
ZOZJY RSYYY IMLRC KDNSF KJVKA WTFNE UFZGS PMXYJ VLKTH WCJNJ
VZLSH IAWKV TQAYE TQFYH KJMHP ISGTL BQRIS OYYLA XXFLI GHTCC
OVXNZ DULNO MKEXT SHLIY LCVVO TIUIB KSBMF XLYTE BAQLB UOMIK
IFWGV SXAOV WZOZY NOVOM UQMMF RFTLZ VH
NPFAY KYCMT XUSWT ZAYVW TSTWC PAHPS TRSFV EBHKR WQWAD DZDSG
DNXLK UEBHY DNDZR KNUVX RBQPD WRNBI DAWRB PYVSL QRYQX AF
I played with this for a while, trying all kinds of things. Obviously, the speed of light (represented in scientific notation by a capital C) must play into it somehow (unless he’s going for a musical key), so variations of “two nine nine…” and “one eight six…” (speed of light in meters/second and miles/second) are tried without success. I also numbered the alphabet from 0 (or from 1) to convert the speed to cjjhjcefi, etc. The previous page in the program included a list of people to whom the conference was expressing gratitude – including Kernighan and Ritchie. Hm. K&R are the “fathers” of the C programming language. But that also got me nowhere. I even tried cribbing text – basically, assuming that the sequence “GMARK” will show up somewhere, and brute-forcing solutions that make that happen. If it works in one place, then I try that key fragment elsewhere to see if other words pop out, and if so, that means I’ll have part of the key figured out. It’s a classical attack, that I’ve never tried before, but it was totally useless here. Damn.
However, I’m convinced that there’s a polyalphabetic cipher at play here, and not a columnar transposition (though “Key of C” also made me check out at least a few columnar attacks, what with the word column starting with C). As a possible variant of that, I even tried sliding rows and columns back and forth based on the digits in C (kind of like his ShmooCon 2009 puzzle). Ultimately, though, none of these worked. And because the frequency distribution of the letters is very flat, it really almost has to be a polyalphabetic cipher.
Finally, after about a day of running a bunch of crazy attacks, and even some drawn-out brute force and dictionary attacks, I put it aside.
Then late on the 28th (or early the 29th, I forget), G. Mark pokes me with a sharp stick, surprised that I hadn’t made any more progress. So I pull the ciphertext out again and keep trying. He confirmed for me that the frequency distribution is “designed to be very flat.” Then he asks me what I think the key is. “299792458,” I respond (the speed of light in meters / second). That’s the right key, he tells me. Now how do I use that? Don’t change it at all, “Use it AS IS,” I’m told. Less than 10 minutes later, I was writing “c…o..n…g…r…” on a post it, and reached for the computer.
Start with the key “299792458.” Begin at the beginning of the ciphertext. Go to the 2nd character, in this case, “C,” and write that down. Then go over 9 characters (“rughucowO”) and write down “O.” Then over another 9 (uugowjzaN). “N.” Over 7 (G). Over 9 (R). And so forth. Here’s the final plaintext:
CONGRATULATIONS YOU HAVE FOUND THE HIDDEN MESSAGE ONE LAST CHALLENGE FOR YOU TO SOLVE LOOK DOWN WHAT YOU ARE HERE FOR IS KEY WHAT THIS LOOKS LIKE IS YOUR PASSPHRASE HURRY X
I wasn’t quite sure how to handle it when I reached the end of the text and wrapped back to the beginning, and so I played a little with the script to see if there was more – but once you reach the end, that’s it. All the rest of the letters are noise. In fact, G. Mark told me they came from a site using, literally, atmospheric radio noise to generate random letters. Hence the very flat frequency distribution.
What’s next, then? Well, “LOOK DOWN” could mean for you to see your badge. That’s the next ciphertext. He talks about “KEY” and “PASSPHRASE” as two different items, which immediately makes me think about a keyed Vigenère, as used on the Kryptos sculpture. KEY might then be “TOORCON,” or “CONFERENCE,” or “TALKS” or somesuch. But what does “WHAT THIS LOOKS LIKE” refer to? The badge itself? Gear, or sprocket, or clock? Or something else?
Another prod from G. Mark makes me look at the last ciphertext itself (the big block of text). What does that look like? “Good luck googling THAT :)” he says. He also tells me it’ll be an “AHA! Moment” when I get it. So I try to relax and just let the answer come to me.
I think about rows of text…prose…paragraphs. Squinting, I can almost imagine it’s marching soldiers – so I play with rank and file and other such words. Then I set it aside again, knowing this isn’t something I can force. About an hour later, it hits me – the Kryptos sculpture. It’s rows and rows of letters, broken up into four blocks (not visually, but there are four different sections to the puzzle).
Finally, I’ve broken the last code. The ciphertext on the badge:
EJGNE EBKJY LEPNS LFQSO UBSNN TIOAC YQRRL KJNYO CRRGG RLPOO TRRML NSGGY IVRTE PYEC
is a keyed Vigenère cipher, using “TOORCONTWELVE” as the alphabet key, and “KRYPTOS” as the passphrase. This gives me the following plaintext:
IHIDE WITHT HEMAN WHOST OPPED THEMO TOROF THEWO RLDDI ALMEB YNAME ANDIW ILLAN SWER
Or, reformatted for easier reading:
I hide with the man who stopped the motor of the world. Dial me by name and I will answer.
ARRRGH! Not only is it Atlas Shrugged again, just like the DEF CON 18 puzzle, but it’s also another BLOODY PHONE NUMBER SNIPE HUNT! Grr. I fight with it off and on over the afternoon, thinking of phone numbers based on characters in the story, looking them up in Google, and finding that most of them have either non-existent area codes or (after I tried calling) are disconnected or local businesses.
Later that evening, though, literally as I was putting my oldest child to bed, it hit me. Quite annoyed that I’d missed it earlier that afternoon, I texted the right answer to G. Mark. (At his request, I won’t post it here – he doesn’t want me to keep burning his various Google Voice numbers :) ).
So, went from zero to the big ciphertext in just a few hours (there was sleep in there somewhere), then put it aside for a few days, then once I went back at it had the whole thing solved in another 12 hours. Not bad. Granted, I was getting some helpful hints from G. Mark, but then anyone at TOORCON would’ve had that as well. In fact, it appears that G. Mark was even selling hints for charity at the con. I don’t know what hints he sold (and would be curious to see them), but I imagine the help I received wasn’t significantly different from they got.
To summarize the various stages of the puzzle:
| Stage | Ciphertext | Cipher | Key |
|---|---|---|---|
| 1 | Morse Code | n/a | n/a |
| 2 | Semaphores | Naval semaphore code | ROT-13 |
| 3 | T-Shirt | Vigenère | GMARK |
| 4 | Back Cover | Multiple Skip | 299792458 |
| 5 | Badge | Keyed Vigenère | TOORCONTWELVE / KRYPTOS |
| 6 | Final Riddle | n/a | n/a |
The most intriguing part of this puzzle, for me, was the encipherment of the back cover text. The “multi-skip” cipher (I’ve no idea if there’s a name for this, so I just made that up) was really interesting, especially with the use of the noise to give the overall ciphertext a very flat frequency distribution. That distribution could easily send an attaker into a polyalphabetic rabbit hole, exactly as happened with me.
Another interesting thought I had about this cipher: You could easily fit a second message in the noise, using a different key. Perhaps additionally hidden with ROT-13 or something else, or perhaps simply hiding in plain sight alongside the more “obvious” primary message. (I’ve already searched, and found no additional messages here. Which doesn’t mean there aren’t any, only that I didn’t find one.)
But is there a way to cryptanalyze this? G. Mark himself gave me a suggestion in that respect – he said that if you looked at a histogram “with period 55,” you’d see spikes corresponding to the digits of the key.
Naturally, I had to write a script to do exactly that. Not being entirely sure what the best approach was, I ended up with something that worked like this:
- Select an overall period of repetition (this works out to the sum of all the digits in the key)
- Sort the ciphertext into that many bins
- See if any of those bins contain an odd distribution of characters
Really, it’s just reformatting the text into X columns, and seeing how the distribution of letters looks for any given column.
The theory here is that for any period, you’d get a mix of hidden plaintext characters and the random filler noise, until you hit on exactly the right period, in which case some number of bins (containing only plaintext, but no noise) would have markedly different frequency distributions. Of course, this tool would have to be simple, fast, and the results easy to scan. Something that made me actually look at full-alphabet distribution graphs for each bin for each period tested – well, that simply wouldn’t work. So I came up with a simple scoring method.
Using the frequencies of letters in the English language, I assigned each letter in each bin a score. “A” shows up 8.17% of the time, so any “A” in a bin is worth 8.17 points. “B” shows up 1.49%, so those are worth 1.49 points, and so forth. I add ’em all up for a bin, then divide by the size of the bin, and that gives me the average frequency of the letters in the bin. More or less.
Next, running this script against the ciphertext, I had to figure out what the appropriate threshold would be. Too high a threshold would only show me periods with bins containing only very common letters, and since even the uncommon letters happen occasionally, that wouldn’t work. Too low a threshold and I’d have too many things to look at. Because of the way the cipher worked, I’d at least be able to throw out any potential key where the last bin in the period wasn’t over the threshold (if the period didn’t end with a key-recovered plaintext letter, then that “key” would really have a shorter period, and so it’d be invalid) (it’s hard to describe, just trust me on this, or better, try it yourself.)
So, running the script with the threshold set at 3 (so the average frequency of the letters in each bin is at least 3%), I get the following: [and note that for all these outputs, I only show the first five lines – they go on for hundreds of lines]
Threshold: 3
4 [1, 1, 1, 1] [4, 3, 4, 3]
5 [1, 1, 1, 1, 1] [4, 4, 3, 3, 4]
6 [1, 1, 1, 1, 1, 1] [3, 3, 4, 3, 4, 3]
7 [1, 1, 1, 1, 1, 1, 1] [3, 3, 3, 4, 3, 4, 4]
8 [1, 1, 1, 1, 1, 1, 1, 1] [4, 3, 4, 4, 3, 3, 4, 3]
Clearly, this isn’t the right cutoff. Virtually every period (the first number on each line) is a candidate. The “keys” generated (the first bracketed sequence, ‘[1, 1, 1, 1, 1]’) are pretty useless. In the case of ‘1 1 1 1 1’ as a key, that’d just be the ciphertext repeated back, in order, with no skipping at all. Have too many 1s and 2s in the key and the solution might be viewable just by looking at the ciphertext and squinting. Finally, the peaks themselves (the second bracketed sequence) don’t look interesting. Increasing the threshold to 4%, we reduce the output somewhat:
Threshold: 4
11 [2, 1, 2, 4, 2] [4, 4, 4, 4, 5]
14 [1, 2, 2, 2, 2, 2, 2, 1] [4, 4, 4, 4, 4, 5, 4, 4]
15 [1, 1, 3, 1, 1, 5, 3] [4, 4, 5, 4, 4, 4, 4]
20 [1, 1, 1, 2, 6, 1, 3, 2, 2, 1] [4, 4, 4, 4, 4, 4, 4, 4, 4, 4]
21 [1, 1, 2, 2, 3, 2, 1, 1, 1, 7] [4, 4, 4, 4, 4, 5, 4, 4, 4, 4]
But there are still far too many candidate solutions. And, again, the keys and peak frequencies look, well, uninspiring. Finally, putting the threshold at 5% generates something interesting:
Threshold: 5
55 [2, 9, 9, 7, 9, 2, 4, 5, 8] [5, 8, 6, 5, 5, 5, 6, 6, 6]
56 [7, 10, 16, 3, 3, 12, 2, 2, 1] [5, 5, 5, 5, 5, 5, 5, 5, 5]
67 [12, 8, 3, 2, 6, 17, 13, 1, 1, 4] [5, 5, 5, 5, 6, 6, 5, 5, 5, 5]
77 [11, 2, 12, 4, 2, 7, 4, 2, 5, 11, 17] [5, 5, 5, 5, 5, 6, 5, 5, 5, 5, 6]
79 [3, 6, 2, 4, 4, 5, 1, 13, 20, 4, 1, 2, 14] [5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5]
Almost all the candidates on this run look interesting, at least from looking at the keys. The first candidate, at key period 55, looks really interesting. Over half of its bins meeting the threshold are actually above the threshold – there are 4 5’s, 4 6’s, and even one at 8%. Finally, the key itself should appear familiar – it’s the speed of light in meters/second. Clearly, this is the answer. Adding in a line to decrypt using each candidate key as it’s derived, we see the plaintext jump right out:
Threshold: 5 (with decryption)
55 [2, 9, 9, 7, 9, 2, 4, 5, 8] [5, 8, 6, 5, 5, 5, 6, 6, 6]
CONGRATULATIONSYOUHAVEFOUNDTHEHIDDENMESSAGEONELASTCHALLENGEFORYOUTO...
56 [7, 10, 16, 3, 3, 12, 2, 2, 1] [5, 5, 5, 5, 5, 5, 5, 5, 5]
UJNRROTLGEBZHAHJOHRJXORHDTIJEIJDLREAEDIRONEMAIOCAEOWANRATODOESBSBTJT...
67 [12, 8, 3, 2, 6, 17, 13, 1, 1, 4] [5, 5, 5, 5, 6, 6, 5, 5, 5, 5]
UNEDYPIAEPTUHHFVIJVUFGNUDEXNQIDRAVSXEOWLANITEANLOAEANWESUXIWRATLSHI...
77 [11, 2, 12, 4, 2, 7, 4, 2, 5, 11, 17] [5, 5, 5, 5, 5, 6, 5, 5, 5, 5, 6]
OUDFYATOAQSKHOCGVRAWEGDTUAEHNHDSEPIARETFNAIEEDWAWTNUGFYUIMRWOLBC...
79 [3, 6, 2, 4, 4, 5, 1, 13, 20, 4, 1, 2, 14] [5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5, 5]
ROOOAQDAXAENTOKHQFAQBEUQYBMTVCCEANCNRENSEBXABENAEMSAEBROAVENCYWO...
It almost appears that I’ve developed a pretty simple tool for detecting, and decrypting, occurrences of this nifty multi-skip cipher. Even if it doesn’t always find the answer right off, it might be a good tool to narrow down to a few ideas to test. So how could G. Mark have prevented this kind of attack? The use of atmospheric noise to make a very random set of filler letters seems, at first, to be pure genius. But because the distribution of the noise is totally unlike the distribution of the plaintext, a script made by a crypto-kiddie like me can (theoretically) bust it open.
So here is what I believe to be an “improved” version of the back cover ciphertext:
ECRRT IREYS OASHT TRFWN NHHUE MGYEA ECLOR RAADV CTANH EULAS
ORKML KATOE ONNEH TSBHO AHWWI OSBTN OOEYM ASHEH NASRE HYNBT
ROVTR OTRAU SHTON RHAUS AHTHK TNFOV SAUTH TEAWO OKSEA FYOCR
RUEMT TNEHE YOUID NTACH IACLB HNNNY AWSOE LANRV THODW OAEFE
IODVO RDOTT OEOED SAIIN PMIGH
ELHON EOARY OTHUS TNABE ASRHY UREUD AEGEY HEHDU TOILU PYGSN
YEWEO RTRDO L
KHRNM AAEAS HNRRN SSSRS GTANT OCIOI HYHOV ALHNE RIHLE LENKE
INEUE UOHOK SEUNO HIAAN GIGIR TWANE RFSRU OSHUO RNMHC AIWYF
OELWI UIOTU IASHG SESTE AOROT OGMNO EEYUS TOOST LTOEA VBWYV
TSAEN LFGEE FEIAO DEWTO ROHOH YOENC KPEAE ONHYD YOGSD WFORT
NYAOA OSEWA HSYFL EPRUA BDHGL SLVTH AFLRU YPEEE TCTEO IUTON
AAESH ROHAF WFHEE HENEU GODAE HRGKN OAARH TOVRV EGOAG OTCEF
TOSOR RDUTE IKYIS ALRSW KNNSM OSTTE ANSSV STSYN DUNOE WOGVA
SAMEH TAOIT TSEIE TUETL NGOHL INFTO TSYNS HFSEN YHRLT KNTSA
OSWER TBHNO YKSAK SUNTB LRVOH MVIIH KSTNO YEAWE SLOTR ALYIE
OLTSO SUETI SHIDY OORSS UVETT RVFOA NAVPO AYYES TOTTS HGSAE
DLISH HSDSR PAHHH EAAYH LRONH AGUOE SVRIS CIAEA HYAYY ELSEU
DDHAE UTWRI ESGRM RYLVE DTYLY YXYIR TRATO GRASF CVKSL YUUHG
RTEHT ARREE ONEE
ARIYS HTNEE AOTFR OENNA AOMON ONOTE TYHUD VXTHD TENAT UVGIO
YTAEE SLEDL EKCVE EBLHG HTYOU EHLFO TAETT TNNEO OOSAI EX
In this case, the filler data is random letters taken from the plaintext itself. So the filler has exactly the same frequency distribution as the plaintext. Which means that my silly little cryptanalysis script is rendered completely worthless. Every key generated, for every key length, is simply “1 1 1 1…..” Anyone attacking this new ciphertext will probably get sucked down into a different rabbit hole (this time, a transposition cipher rabbit hole).
Is it really better? I don’t know. It might be, but then again, I’m just a beginner here. I could be missing something important.
Anyway, the bottom line is that this was yet another fun puzzle from G. Mark. I’m glad he was able to share with me the details of the puzzle after the con completed, so that I could have the thrill of solving the challenge. And finding a totally new crypto scheme (and possibly even improving upon it) definitely made this a memorable victory.
Thanks again, G. Mark!
UPDATE: For fun, I tweaked the “improved” back cover ciphertext. Sharp-eyed readers may notice that it’s a little bit longer than the original. There’s now a second message embedded in the noise… I’ll even give you a hint: Counting begins at position 4, not 1 (to avoid crashing into the original hidden text). And the key is in this page’s URL.
(view Archived Comments from the old site)

